Our Blog
Web browser text search
So I am working on a project where I have to search some HTML documents for a possible text string. This lead me to an interesting find in how browsers do searching on text. Let's look at the following HTML. <div><div style="background-color:...
Find out what Subversion commits haven’t been merged to stable
We frequently use Subversion for version control, and use /trunk to commit all code in active development and merge code to a stable branch that represents what is currently on a production server. Sometimes commits need to be done right away, so you merge them right...
Using nullmailer as a simple MTA
nullmailer is a very simple MTA I like to use on Linux servers when I don't want to have a lot of hassle with mail server configuration. It will automatically send all local mail to one of my email addresses by simply installing it and configuring two files. The...
Does Your Business Need a Mobile App?
As a business owner you may be asking yourself this question when it seems like the whole world is going mobile. There are some key points to consider in order to answer this question for your company. The first thing to consider is your audience. What does your...
Gaming to Grow Your Business
The Economist says "video games will be the fastest growing and most exciting form of mass media over the coming decade." But why should that excitement end there? Businesses across the board are finding they can use the same idea, and the same audience, to increase...
Html5 Audio restart playback in iOS Safari
When using html5 audio and Apple's safari browser on iOS there is a problem that occurs when you try to set the audio's time. Html5 audio DOM object has an attribute called currentTime. This unfortunately isn't available in iOS safari. This makes it difficult if you...
New mobile app – Vinny
We are excited to showcase a fantastic new mobile app we have helped develop. This app is still in beta but will be released soon! Did you ever wonder what the dealer really paid for that car on the lot? Check out Vinny, a new app that tells you the exact wholesale...
Automatic and Secure rsync over SSH
Let's you want to set up an automatic rsync over ssh to a remote server, but you want to do it in a secure way. Using rsync over ssh is a convenient way to have all of the power of rsync for synchronizing files, comparing differences, doing backups, without having to...
Call out to Early Adapters: Could Smart Stickers Add Value to Your Business?
Smart stickers, or programmable tags, are low-cost pieces of paper or plastic that can communicate with gadgets via a short-range radio technology called near field communication, or NFC. They can be customized to trigger an action on any phone with an NFC chip....
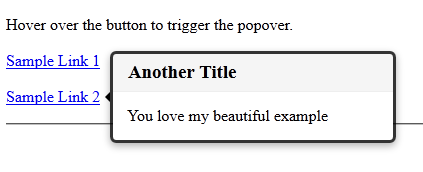
A Simple Popover Tooltip
I like the popover tooltip that Twitter designed and I want to use it in my web applications without having to include the full bootstrap project. I included only the basics needed to give me the popover functionality. Here is what it looks like once implemented: To...
Guru Technologies
Contact Us
1645 E Hwy 193, Suite 103,
Layton, UT 84040
(801) 528-1195
contactus@gurutechnologies.net